

Neurological disorders such as Parkinson's disease, Alzheimer's disease, brain tumors, and epilepsy pose significant global health challenges due to their diagnostic complexity, increasing prevalence, and profound impact on quality of life. Despite some challenges, classical methods remain crucial in the diagnosis and prognosis process. Furthermore, the recent advancement of artificial intelligence in the automated, accurate, and efficient analysis of complex biomedical data has paved the way for improved diagnostic processes.
Therefore, this study examines methodological trends in Artificial Intelligence applications for the diagnosis of major neurological diseases over the past five years (2021-2025). A bibliometric analysis was conducted in the Web of Science and Scopus databases using disease-specific search queries. Open access journal articles were included in the study and the data were analyzed with VOSviewer after word filtering involving artificial intelligence methods to identify dominant algorithms and annual trends. Convolutional Neural Networks are the most widely used method across all neurological disease groups, particularly in the study of brain tumors and Alzheimer's disease. While Support Vector Machines are prominent in Parkinson's disease research, Artificial Neural Networks and Recurrent Neural Networks are gaining more prominence in epilepsy and Alzheimer's disease studies. Long Short-Term Memory Networks play a significant role in the analysis of time-series EEG and motion data in epilepsy and Parkinson's disease.
The aim of this research is to examine how semi-autonomous robot assistants can be applied in higher education (HE) to support both instructional and administrative processes.
The work is motivated by challenges such as increasing administrative demands, shortages of teaching assistants, declining student engagement, and the limited availability of timely feedback. To address these issues, three main scenarios are being supported with a development of robot assistant tooling/toolbox:
The study employs a mixed-method and action research design, including pilot implementations, iterative refinements, and classroom experiments. The objective is to build a toolbox that illustrates practical applications of robot assistants in HE and provides empirical insights into, acceptance and usability of robot assistants in HE, and the potential to promote more inclusive and interactive learning environments. This research contributes to digital transformation of education and explores how semi-autonomous robots can be meaningfully integrated into teaching and learning practices.
This paper presents the procedure of setting a 5G network for Technobothnia laboratory using Firecell solutions.
The procedure includes 5G frequency band allocation, range coverage calculation, IP network configuration, 5G parameter tuning, and corresponding communication performance test results. The paper can be used as a reference for setting private 5G networks.
Metropolia University of Applied Sciences has launched the Metropolia Tech Pathway online studies to support international students entering engineering degree programmes in Metropolia UAS. The pathway program responds to Finland’s growing demand for global talents in the field of technology.
Metropolia UAS has long experience in running international programmes and this experience has highlighted the importance of students’ social and cultural integration for both academic progress and wellbeing. One of the success factors for international students is their ability and readiness to adapt to Finnish study practices and everyday life. To address this, Metropolia launched the Tech Pathway program.
Starting in January 2025, the Tech Pathway program offers international students an affordable opportunity to begin engineering studies while gaining valuable first-hand experience in a Finnish higher education environment. The programme combines coursework, guidance and orientation to support a smooth transition into degree studies.
The presentation will introduce the Tech Pathway program, outline its implementation and benefits for students and degree programmes. It will also discuss how such initiatives can enhance the attractiveness of Finnish higher education and contribute to the availability of skilled professionals.
In today’s world with an uncounted number of applications and services being used by a countless number of users fast, reliable and even more important: secure authentication of users is crucial for individuals, organizations and companies around the world. While the combination of user name and password was common for long time in many systems, due to phishing and other attacks more secure authentication methods are needed. Passkeys are a promising and strong alternative to passwords.
This paper will give insight into the idea and priniciples for passkeys. In addition it will address the benefits that passkeys provide as compared to conventional passwords. In the first section we will address passwords from a cryptographic perspective: Passwords correspond to a symmetric crypto system, where the secret password must only be known by the user and the corresponding application server. We will see that passwords have quite some disadvantages. Apart from the possibilities of guessing simple passwords users may apply (e.g. summer25), passwords are subject to phishing and other attacks. Therefore, more sophisticated methods for user authentication are needed for today’s applications and services. At this point the FIDO organization [1] and passkeys come into the game [2]. The idea of passkeys is based on the principle of asymmetric crypto systems. For such systems the smartphone or laptop user creates a key pair that consists of a public key and a private key. The public key will be sent to the application server and allows anyone to encrypt a specific plain text message. However, due to the fact, that the creation of the above mentioned key pair makes use of so called trapdoor or one-way-functions, decryption of an encrypted message is only possible by using the private key.
Therefore, only the smartphone or laptop user may decrypt a specific encrypted message. This idea will be described in this paper by using the RSA crypto system [3]. Within the presentation it will be shown, that RSA is based on the socalled integer factorization problem. RSA requires the exponentiation of an integer x, the plain text, with the public exponent e modulo a large composite number n, where n is the product of two large primes p and p. Although it is not possible to factorize n into its prime factors p and q for any third party, it is possible for the smartphone user to calculate Euler’s Phi-function Φ(n) = (p − 1) ∙ (q − 1). By doing so, it is possible for the user to compute the multiplicate inverse d= e-1 mod Φ(n), which is needed to compute the plain text xout of an encrypted cipher text y = xe mod n. Within this paper we will also show a simple cryptographic protocol based on RSA which may be used for secure user authentication. This protocol contains the advantage, that no secret password or the like needs to be stored on the application server, nor does the system suffer from possibly ‘simple’ passwords. Passkeys and the used protocols are always strong and are phishing resistant. Therefore passkeys will receive more attention and will most likely be the authentication method for many – possibly all – future applications and services.
References:
[1] wikipedia, „FIDO-Allianz,“ 01 September 2025. [Online]. Available: https://de.wikipedia.org/wiki/FIDO-Allianz.
[2] FIDO Alliance, „passkey central,“ [Online]. Available: https://www.passkeycentral.org/home. [Zugriff am 01 09 2025].
[3] C. Paar und J. Pelzl, Understanding Cryptography, Heidelberg: Springer Verlag, 2010.
Managing the vast amount of devices and data involved with IoT is one of the main challenges in various domains, such as smart city sensors, intelligent transportation systems, industrial robots, autonomous vehicles[1][2][3]. Scalability along with portability becomes a major obstacle when millions of devices are potentially connected and interacting. With its capacity to autonomously scale systems and down in response to demand, Kubernetes is revolutionizing the Internet of Things by enabling resource management and ensuring optimal performance even as the number of devices increases.
IoT apps may be deployed on any system—edge, local, private, or public—and moved to a different environment as needed with Kubernetes. KubeEdge is an extension of Kubernetes that integrates the container orchestration of Kubernetes with the particular needs of edge computing. It supports many edge protocols and makes it possible to manage edge nodes and devices as part of a Kubernetes cluster, and offers a flexible option for a variety of edge computing applications.
Our innovative work realizes an open-sourcei integrated framework, as shown in Figure 1, involves edge and micro-edge devices seamlessly integrated via extended KubEdge-managed nodes offering:
• Cloud to Edge and Edge to Cloud traffic routing with software multicast support
• Uniformity to manage the heterogeneity of the Leaf-Edge-Devices (LEDs)
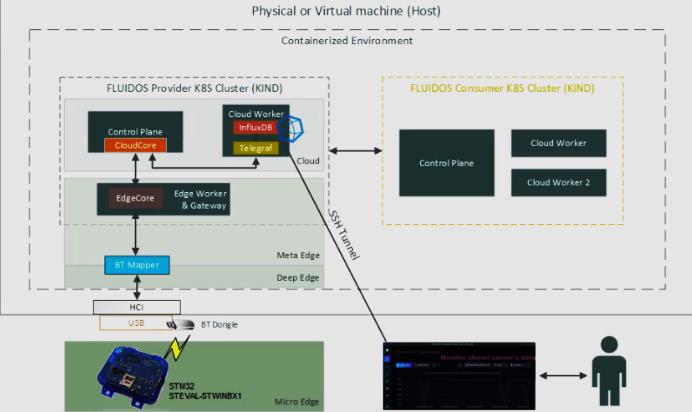
In particular, this involves a fully automated process tailored for Edge-IoT scenarios. This is achieved using a customized version of KIND, which has been extended to support the deployment of Edge worker nodes as the foundational platform. Following the deployment of the testbed, the novel component EdgeResourceManager automatically generates Sensor-type Flavors, derived from the registered devices and the metadata detailing their available sensors. All the required information is acquired by leveraging the Edge API. Once a consumer purchases one or more sensors, the extended RouterManager, part of the CloudCore component, is responsible for configuring the KubeEdge Router component to establish data links between the sensor outputs and the consumer's specified target endpoint(s). These endpoints may reside on the provider’s or consumer’s premises, or on a third-party cloud platform, provided they are accessible to the Router.
The Figure 2 next illustrates such a scenario, in which the consumer has allocated sensor data from two Micro Edge devices. The data is forwarded to two distinct target endpoints, corresponding to the consumer’s requirements as defined in the established contract by the two clusters.
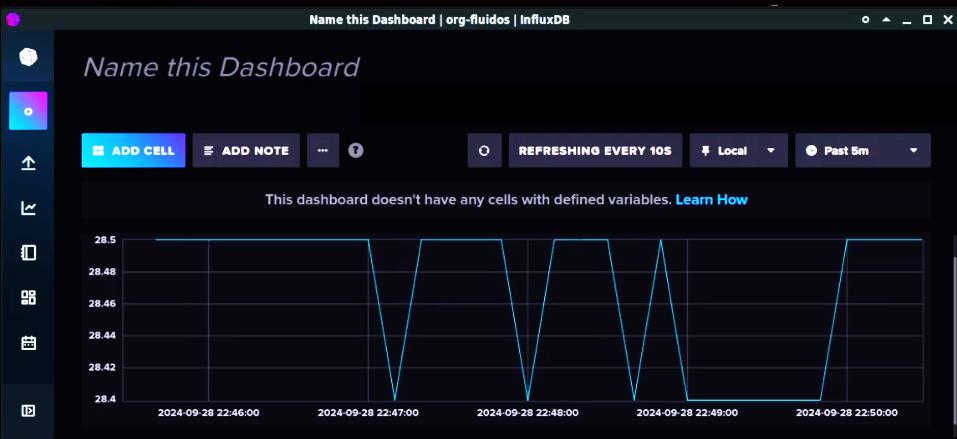
Overall, this novel approach facilitates dynamic collaboration and the best possible use of existing capabilities by connecting users who want to run code on these third parties' resources. By providing access to a range of edge resources and guaranteeing security and adaptability, we revolutionize the deployment and management of applications while satisfying the unique requirements of users in an environment that is becoming more interconnected. This strategy may not only increase operational effectiveness but also spur innovation across other industries, increasing the accessibility and applicability of edge computing technology.
Acknowledgment
This work was supported in part by the European Union (EU) Horizon 2020 Project FLUIDOS (Flexible, scaLable, secUre, and decentralIseD Operating System) under GA No. 101070473
References:
[1] S. Dustdar, V. C. Pujol, and P. K. Donta, “On distributed computing continuum systems,” IEEE Transactions on Knowledge and Data Engineering, vol. 35, no. 4, pp. 4092–4105, 2023
[2] C. Figueroa, T. Knowles, V. Kukreja and C. -H. Lung, "IoT Management with Container Orchestration," 2023 IEEE 3rd International Conference on Electronic Communications, Internet of Things and Big Data (ICEIB), 2023, pp. 49-54
[3] M. AlSelek, J. M. Alcaraz-Calero and Q. Wang, "Agile AI and Firmware Management in IoT: DevOps for Low-Power Microcontroller-Based Platforms," 2024 9th International Conference on Smart and Sustainable Technologies (SpliTech), Bol and Split, Croatia, 2024, pp. 1-6, doi: 10.23919/SpliTech61897.2024.10612585.
https://github.com/fluidos-project/fluidos-edge
==> Abstract (PDF)Introduction
We are developing platforms that shall help students to build practical competencies by working on challenging tasks in creative
and highly motivating applications. Several of these are systems that autonomously learn to master control tasks.
Such systems are typically based on deep reinforcement learning (DRL), and related algorithms are frequently demonstrated by
agents that learn to play games. This submission reports on first results related to a platform where AI agents
learn to manoeuvre balls through virtual and physical hardware mazes while avoiding dropping into holes.
Target platform
The system contains
two environments (Fig. 1): a software simulation and a motorized physical maze. The former shall serve to develop and demonstrate DRL
agents without hardware and physical time constraints during training. The latter shall demonstrate virtually trained agents on a physical device.
From education perspective, it applies fields like deep learning, image processing, computer science, physics, electronics, and mechanics in an interdisciplinary way.
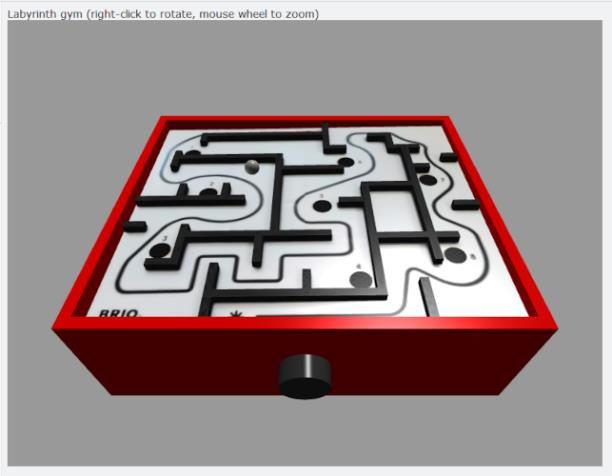

Figure 1: 3D software simulation (left) and automated physical maze (right)
Reported results
We have developed a fully functional virtual environment, which correctly simulates the related physics and contains six different maze layouts,
including all layouts of the game hardware. Noteworthy, we have succeeded to develop Deep Q-Learning (DQN) agents, which are capable to
manoeuvre balls from start to finish, for all maze layouts.
Related to the physical demonstrator, we have motorized the game hardware and developed a highlevel Python interface to control the game as well as low-level motor control by a connected microcontroller. Moreover, we have integrated an industrial camera required to detect the system’s state (e.g., ball location).
Work-in-progress and prospect
At the time of writing, we are developing
image processing methods for the physical maze. These shall allow us to address the transfer of virtually trained AI agents to the physical device.
Future aspects may include the following:
▪ Improved image processing to capture the maze layout
▪ Integration of NVIDIA Jetson boards
▪ Experiments with different DRL approaches and reward systems
▪ Fine-tuning of virtually pre-trained agents using the physical device
▪ General AI agent capable to solve maze layouts which it has not seen before
The presentation will report on the experiences gained during the three-year ROBUST project. During this time, Pepper-type semi-humanoid robots were used continuously throughout the entire project period in a number of care facilities.
The applications for cognitive and physical activation were developed and evaluated in a participatory manner with the involvement of local specialists. The results provide interesting insights into the effectiveness, customizability, and acceptance of such semi-autonomous systems in real-world contexts, thus pointing the way toward the future sustainable development of intelligent systems in the care and support context.
==> Abstract (PDF)a developer, allows one to rapidly prototype ideas. The focus of the developer shifts from programming to prompting things into existence. AI-based tools for programmers become more powerful on a daily basis: Tools like Github Copilot, Claude Code and their integration into IDEs such as Jetbrains, Cursors or VSCode promise to accelerate development times and shift the developer attention away from implementation to integration and validation.
This paper evaluates the usefulness of AI-systems to rapidly implement a C++ program for real-time testing synthetic drum models. Two publications written in Swedish language – which the Author of this paper is not proficient of –, available in pdf format were used as input data. They contain text and graphics illustrating the DSP-blocks of the synthesis models at an abstract level. As a first step ChatGPT was instructed to interpret those papers, which were uploaded in their original pdf form, and generate C++ classes of their implementation including a description of the model parameters. The resulting source code was moved to an empty Jetbrains CLion project. With the help of the plugin version of Github Copilot in Agent mode (preview at the time of the writing), the AI was instructed to create a project structure, using CMake as a built system, DearIMGui and RtAudio as libraries for graphical UI and real-time audio IO and Github Actions for pipelined CI/CD.
It was possible to create a working C++ application in a few hours, which faithfully represents the drum models, allows for DSP parameter tweaking and real-time visualization of the generated waveforms both in time-base and spectrogram view.
In conclusion, Agentic Coding allows rapid prototyping within hours compared to days or weeks. The generated code requires further quality assessment and review.
References:
https://agentic-coding.github.io/
https://github.com/ctag-fh-kiel/md-drum-synth
Data analytics is the process of studying raw data to extract insights, identify trends, and make knowledgeable choices. It involves using various techniques and tools to analyze large and complex datasets to extract insights that can be used to solve various problems, improve processes, and drive innovation. Key aspects of data analytics are
1) data collection, which is gathering data from various sources,
2) data cleaning and preparation, which ensures the data is accurate, complete, and ready for analysis,
3) data analysis by applying appropriate techniques to analyze the data and extract sensible information,
4) interpretation and visualization, which means presenting the findings in a clear and comprehensible way, and
5) sharing insights through communicating the findings to stakeholders to advise decision-making and drive action.
There are many types of data analytics tools for different purposes. Examples of data analytics tools are SQL databases for data collection and storage, OpenRefine for data cleaning and preparation, Python with libraries like pandas for data analysis and modeling, Power BI for business intelligence, Apache Spark for big data and real-time analytics and Grafana for data visualization.
==> Abstract (PDF)Intermediate topics in Cybersecurity is a three year European-funded project dedicated to raise awareness and strengthening the knowledge gap on cybersecurity. By fostering a network of experts and promoting cyber resilience, the project aims to establish the project’s methodology as a recognized standard in cybersecurity education. Its activities span the creation of an online course focusing to four modules, namely
i) Organised disinformation and threats in social media
ii) Standards and recommendations in cybersecurity management
iii) ENISA cybersecurity skills framework and
iv) Use of AI in cybersecurity.
Each module will comprise a syllabus, 50-100 pages of text & graphic content, an online lesson (60-90 mins. of audio and images), an introductory video (5-10 mins.), exam questions and quizzes, case studies with branching scenarios and a 20 page teachers’ book with additional ideas for use in a regular classroom setting (group activities, discussion topics etc.).
The expected outcomes include a significant boost in cybersecurity awareness and skills across students, the creation of an advanced training program tailored to today’s needs and enhanced capabilities among instructors to teach cybersecurity effectively.
==> Abstract (PDF)The African BlendEd Course (ABC) is a three-year initiative funded by the European Union, designed to enhance student engagement and develop essential skills for the labor market. By bringing together students from diverse countries and academic disciplines to collaborate on community-based projects, ABC fosters enthusiasm and cultivates core competencies such as teamwork, entrepreneurship, critical thinking, and communication.
This project builds on a longstanding collaboration that began in 2008 among European universities that pioneered the BlendEd model. These institutions, now part of the ABC consortium, continue to innovate in blended learning and international education. The consortium includes eleven partners from seven countries, united by a shared mission to empower African universities—particularly in the agricultural sector—to design and deliver blended courses that generate real-world impact. The project also aims to expand this model to other disciplines and regions across Africa.
ABC’s overarching goal is to boost student employability through experiential, interdisciplinary learning while delivering tangible benefits to local communities. It encourages the adoption of BlendEd courses by students, educators, and industry stakeholders, and promotes widespread uptake of the model across African higher education. By embedding collaboration, innovation, and community relevance into education, the project equips students to thrive in a dynamic global workforce while contributing meaningfully to their societies.
==> Abstract (PDF)CyberSEA is a European-funded project -currently on its second year-, dedicated to strengthening cybersecurity within the maritime industry. Its primary goal is to raise awareness and deliver targeted training to cadets and seafarers, ensuring they are equipped to defend ships and cargo against cyber threats.
By fostering a network of experts and promoting cyber resilience, the project aims to establish the CyberSEA methodology as a recognized standard in maritime education. Its activities span the identification of vulnerabilities in the sector, the creation of specialized training materials, the development of remote labs and a virtual hub, and the launch of an online course. he expected outcomes include a significant boost in cybersecurity awareness and skills across the maritime workforce, the creation of an advanced training program tailored to the merchant marine sector, enhanced capabilities among instructors to teach cybersecurity effectively, the establishment of remote labs and a centralized hub for hands-on learning, and a broader adoption of cybersecurity best practices throughout the industry.
==> Abstract (PDF)This research aimed to evaluate the use of high-level synthesis (HLS) within the hardware-software codesign paradigm with application to efficient implementation of convolutional neural networks (CNN) for birds vocalization classification.
The classification model was trained using supervised learning with selected and preprocessed bird vocalizations from the Xeno-Canto database of wildlife. The preprocessing and feature extraction of the audio data involves noise reduction, silence removal and calculation of psycho-acoustically weighted MEL spectrograms which were used for CNN model training. With the applied Sequential CNN classifiers an accuracy of approx. 94% was achieved.
For implementing on an AMD Zynq UltraScale+ MPSoC, the Python solution of the classifier was analyzed module by module with a focus on the design principles of hardware software co-design and HLS. Depending on the requirements of the module, preprocessing and feature extraction modules are implemented either as software, hardware description language (HDL) or HLS-based hardware acceleration, while CNN inference is performed on the processing system using the PYNQ framework. The different variants are compared in terms of latency, resource usage and development effort.
The evaluation showed that HLS is highly effective for abstract, dataflow-oriented signal processing tasks, such as spectrogram generation. It can significantly reduce development time without compromising performance. However, traditional HDLs remain superior for low-level interfaces such as I2S audio input due to their precise control over timing and protocol details. The CNN implementation using PYNQ has shown that high-level frameworks can effectively integrate with custom hardware modules to create a cost-efficient, real-time audio classification system on an SoC.
==> Abstract (PDF)For many critically ill patients, artificial ventilation is required. In intensive care, this is often performed using a tube that is inserted into the trachea. This endotracheal tube that must remain in the correct position over an extended period of time. At present, the tube placement position is checked at short intervals by medical staff through visual inspection.
An experimental system for automated monitoring based on magnetic localization is presented, considering both technical feasibility and medical applicability. For this purpose, a ring-shaped permanent magnet is attached to the tube, and a device placed outside the patient detects the magnetic field. This device measures the field components using 64 magnetic sensors arranged in an 8×8 matrix. From these amount of vector data, the position of the tube is continuously estimated.
Two approaches to sensor data fusion are investigated interdisciplinary:
(I) Two-dimensional image similarity – cross-correlation of vector-valued sensor maps, in which a reference matrix is compared with the current measurement.
(II) Model-based localization – the inverse problem is solved by adjusting the position and orientation parameters of a magnetic field model.
This is achieved by stepwise stochastic optimization in order to minimize the deviation between the model and the measured data.
Both methods can be realized with reasonable computational effort and enable continuous real-time monitoring. The system triggers an alarm as soon as an impermissible displacement is detected, and can thus provide early indications even of small positional changes. In this way, a contribution could be made to improving patient safety.
==> Abstract (PDF)In an ambitious move to revolutionize the European manufacturing landscape, a consortium of leading educational institutions, innovative small and medium-sized enterprises, and industry clusters from across Europe have joined forces to launch the "Digital Twin on Smart Manufacturing" project. This initiative has been made possible through the Erasmus+ programme, project number 101140156.
“Digital Twin” concept involves creating a virtual model of a physical object, process, or system. This digital representation is designed to accurately mirror the real-world counterpart in all its aspects, from physical properties and behaviours to processes and performance. The purpose is to allow for simulation, analysis, and control of the entity in a virtual environment, which can lead to insights and actions that improve the real-world counterpart's efficiency and maintenance.
The "Digital Twin on Smart Manufacturing" project aims to create a comprehensive European Digital Twin Skills ecosystem. The project will deliver an integral curriculum catering to the emerging professional needs of mid to high-level Information Technology and Operational Technology technicians across the European Qualifications Framework (EQF) Levels 4-8. This curriculum will be available in English and 5 other European languages, ensuring wide accessibility.
The primary objective of the project is to enhance the capacity of educational and vocational training providers to align their offerings with the dynamic requirements of the manufacturing industry. This is expected to result in several tangible outcomes, including:
To achieve these goals, the project will develop and disseminate a range of transformative educational resources and tools, including:
The consortium comprises 2 VET providers, 1 HVET provider, 2 higher education institutions, 4 SMEs, 1 industry cluster, and 1 chamber of commerce from 5 European countries - Italy, Spain, Greece, Sweden and Bulgaria.
The project aims to facilitate fostering a skilled workforce equipped with the latest digital twin technologies, and thus make a significant contribution to the European Green Deal, the digital transformation of Europe, and the support of small businesses. The creation of Digital Twin occupation profiles and issuing micro-credentials will further solidify the project's long-term impact on the European labour market.
==> Abstract (PDF)Today, measuring instruments are essentially measurement computers, and automated test systems would be can only be implemented economically through internal device information processing.
While sequential controls can still be implemented with simple microcontrollers, measurement data processing sometimes requires powerful signal processors or even real-time processing.
Due to their flexibility and inherent parallel processing potential, Field Programmable Gate Arrays (FPGAs) are increasingly being used in measurement and test technology.
In this article, the author will present his own previous work as well as future-oriented concepts.
One example is the Cyber Physical Test System (CPTS), which offers small and medium-sized enterprises a low-cost perspective for the production testing of embedded systems. CPTS is essentially based on an integrated circuit (IC), namely a so-called FPGA platform IC, and uses the concept of synthetic measuring instruments or, more briefly, synthetic instruments (SI). By partially configuring the FPGA with SIs on a case-by-case basis, comparatively "small" FPGAs can be used, thus saving costs. From a cost perspective, simulated sensors can also be integrated using the same principle. Even more conceptual is the idea of a Digital Twin (DT) emulating units under test (UUTs) in real time using FPGAs, thus enabling the early creation and evaluation of test programs before a physical UUT even exists. Behavioral failure modes can be emulated even before the structure of a UUT is known.
Finally, the concept of DT is "turned around" to the emulation of automatic test equipment (ATE) with the goal of "ATE-agnostic" execution of test programs.
==> Abstract (PDF)Osteoporosis is a metabolic bone disease that is underdiagnosed and undertreated. It can lead to vertebral fractures involving pain and decreased mobility. Recent advancements in artificial intelligence offer promising solutions to automatically check available medical images like computed tomography (CT) scans, which are acquired for other medical indications (”opportunistic screening”), for indicators of osteoporosis like vertebral fractures and to assess the risk of future fractures.
In this talk, we present our pipeline for automatic vertebral fracture prediction from CT images based on extracting individual vertebral patches which are analysed using a Convolutional Neural Network (CNN) to obtain a score to classify whether the subject will experience a vertebral fracture within 10 years. This score is then used in an age- and body mass index (BMI)-adjusted Cox proportional-hazards model to compute an individual vertebral fracture risk. We will also discuss experimental results to improve the CNN-based osteoporotic vertebral fracture prognosis by self-supervised pre-training as well as preliminary results and challenges of applying large vision language models (e.g., Merlin) for this task.
Experimental results are obtained on the publicly available MrOS (Osteoporotic Fractures in Men Study) dataset.
==> Abstract (PDF)Collision hazard detection in dynamic outdoor environments—such as construction and mining work zones—remains a critical challenge due to unstable signal conditions, mobility-induced fluctuations, and frequent non-line-of-sight (NLOS) scenarios. While camera-based visual detection is widely used, its performance degrades in dusty or obstructed conditions. Similarly, high-precision localization methods like Ultra-Wideband (UWB) and GPS are often cost-prohibitive and lack scalability.
Bluetooth Low Energy (BLE) offers a cost-effective and widely available alternative, but its Received Signal Strength Indicator (RSSI) is highly variable and sensitive to multipath effects and environmental changes, limiting its real-time reliability.
This paper presents AlertBLE, a hybrid BLE-based localization and hazard detection system designed to enhance work zone safety alert mechanisms. AlertBLE combines an Extended Kalman Filter (EKF) and an Adaptive Moving Average (AMA) algorithm to dynamically stabilize RSSI signals by accounting for LOS/NLOS variations.
Additionally, machine learning (ML) classifiers—K-Nearest Neighbors (KNN) and Support Vector Machines (SVM)—are employed to improve hazard detection accuracy under mobility-induced signal dynamics. The system includes wearable proximity sensors for personnel and portable vehicle-mounted detection units, enabling continuous monitoring and immediate alerts during vehicle movement or reversing. Extensive field evaluations in realistic outdoor environments demonstrate that AlertBLE effectively detects hazards, enhances situational awareness, and significantly reduces collision risks in work zones.
==> Abstract (PDF)One of the most challenging task during the implementation of the international projects is to develop the educational content,
which could allow students with different backgrounds and different levels of the language of instructions to achieve the required competences withing the one course.
The other new challenge which academicians are facing is the integration of the generative software into the educational process in the way that it could help students
to gain the knowledge and not just replace the educational activities.
As the case study authors consider the implementation of the project-based approach used in the course “Applied Embedded Systems” within the international Master Program “Embedded Systems Engineering” in the FH Dortmund and its future scaling for the implementation in the virtual Master School within the DAAD-funded project UA4PIM: University Alliance for Project and Innovation Management .
==> Abstract (PDF)In the engineering programmes of Finnish Universities of Applied Sciences, the nominal study time is eight semesters, comprising a total of 240 ECTS credits. The final compulsory part of the studies is the final-year project (15 ECTS), usually carried out individually in collaboration with the engineering industry and reported in the form of a written thesis. The project’s 15 credits correspond to a nominal workload of half a semester (approximately eight calendar weeks). Unfortunately, this limited time is often insufficient to plan, implement, and report the project. In practice, the duration from project definition to final documentation and presentation in the thesis seminar typically exceeds one semester. This delay frequently results in the prolongation of studies.
The funding of universities by the Ministry of Education is largely based on the number of graduates, with higher funding awarded for graduates completing their studies within the nominal four-year period. Prolonged studies therefore have a direct negative impact on funding. The Ministry also sets annual targets for the number of graduates, and failure to meet these targets leads to further funding reductions. Until now, the number of graduating engineers in the School of Smart Solutions at Metropolia UAS has been between 300 and 350 per year. The set targets are 400 graduates for 2025 and 450 for 2026.
Consequently, changes to the thesis project process are essential, as it is clearly a major factor in study delays and, in some cases, in students not graduating at all. A development project to improve the process was launched in autumn 2024, with the first pilot implementations in spring 2025. From the beginning of 2026, all projects will follow the revised principles.
This paper describes the improved process, the reasons for the reform, and preliminary results.
==> Abstract (PDF)This lecture will provide insight into a newly developed course on Embedded Security. Taking a practical approach, the course covers various methods used to hack hardware, aiming to make students aware of potential security risks in embedded systems.
Topics range from simply monitoring communication channels such as I²C, SPI, and CAN, to more advanced techniques like power analysis, power glitching, and clock glitching.
==> Abstract (PDF)In this paper the B-SaFFeR project is presented, with its goals, ambitions and results.
The Rwenzori Mountains in Uganda are increasingly affected by flash floods, resulting in severe human and socio-economic losses. The B-SaFFeR project, funded by VLIRUOS, seeks to strengthen local capacities for disaster risk reduction through a combination of low-cost technology, hydrological modelling, and community engagement.
A sensor network integrating rainfall gauges, radar river level measurements, and CCTV-based computer vision has been deployed to collect real-time meteorological and hydrological data. Data are transferred via low-power 4G connections to the APTERRA cloud platform, enabling open access for researchers and supporting the development of a spatially explicit hydrological model.
Preliminary results demonstrate successful installation and validation of monitoring stations, alongside capacity building with local partners to ensure knowledge transfer and system sustainability. Future work will integrate AI-based flood prediction, citizen-driven data collection, and watershed modelling to design a proof-of-concept flood early warning system. By coupling technological innovation with socio-economic resilience mechanisms and stakeholder co-steering, B-SaFFeR aims to deliver long-term academic, community, and policy impacts in the Rwenzori region.
==> Abstract (PDF)